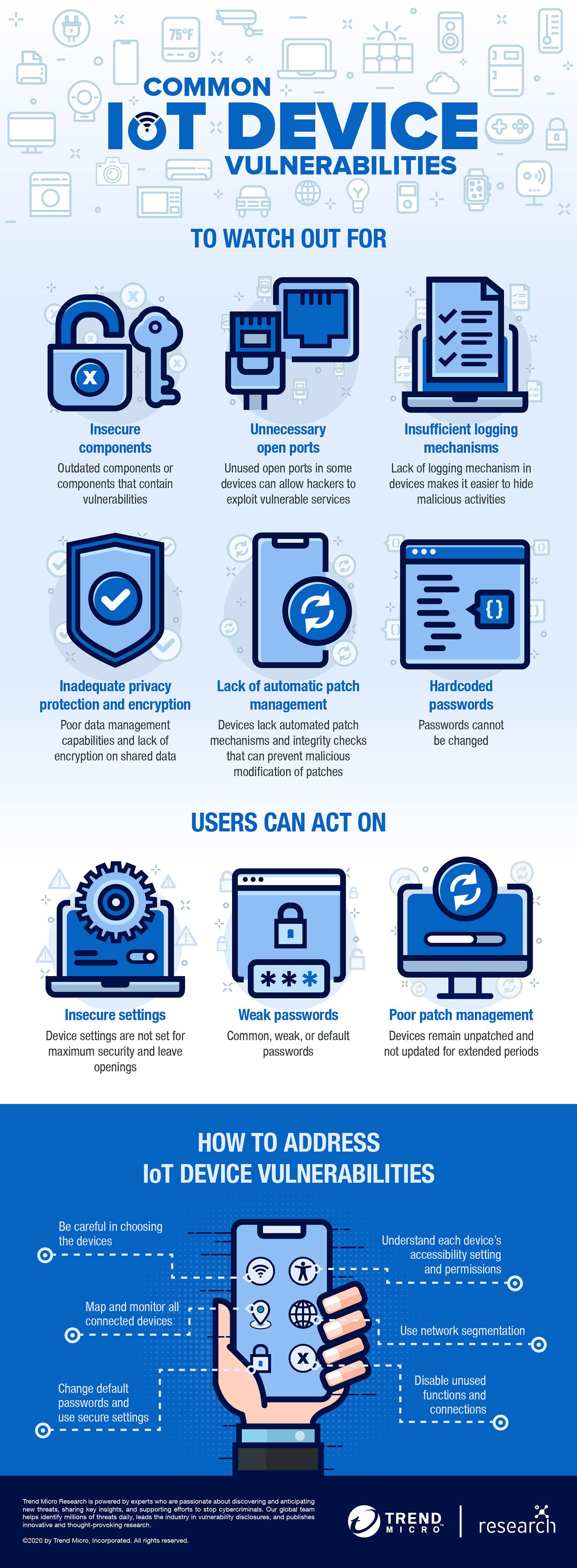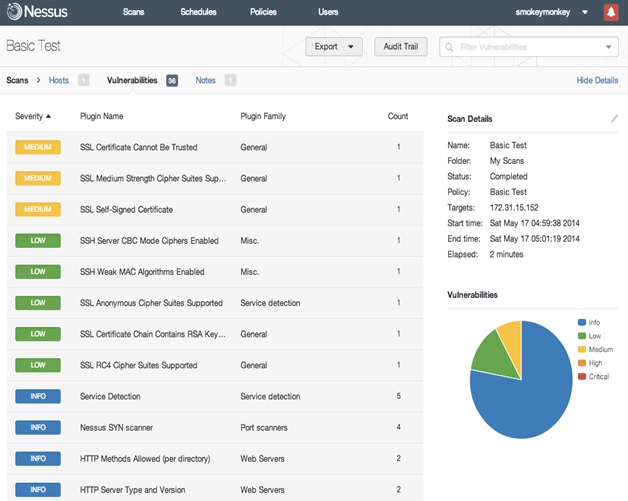
IOT Vulnerability Assessment using Raspberry Pi2 - Cyber Security Blogs - IoT Security - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata
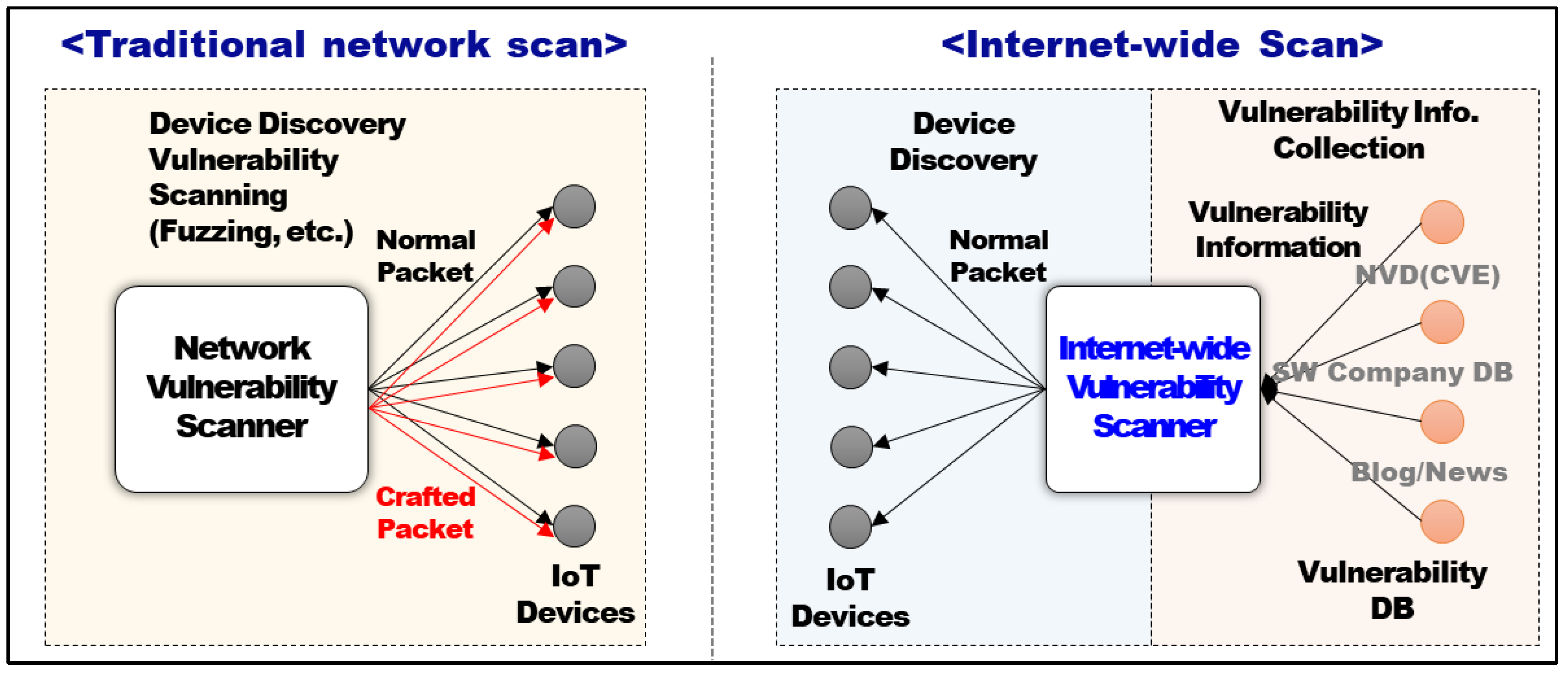
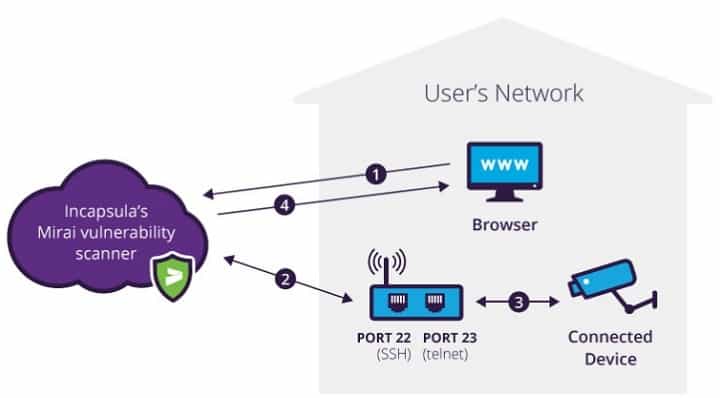
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
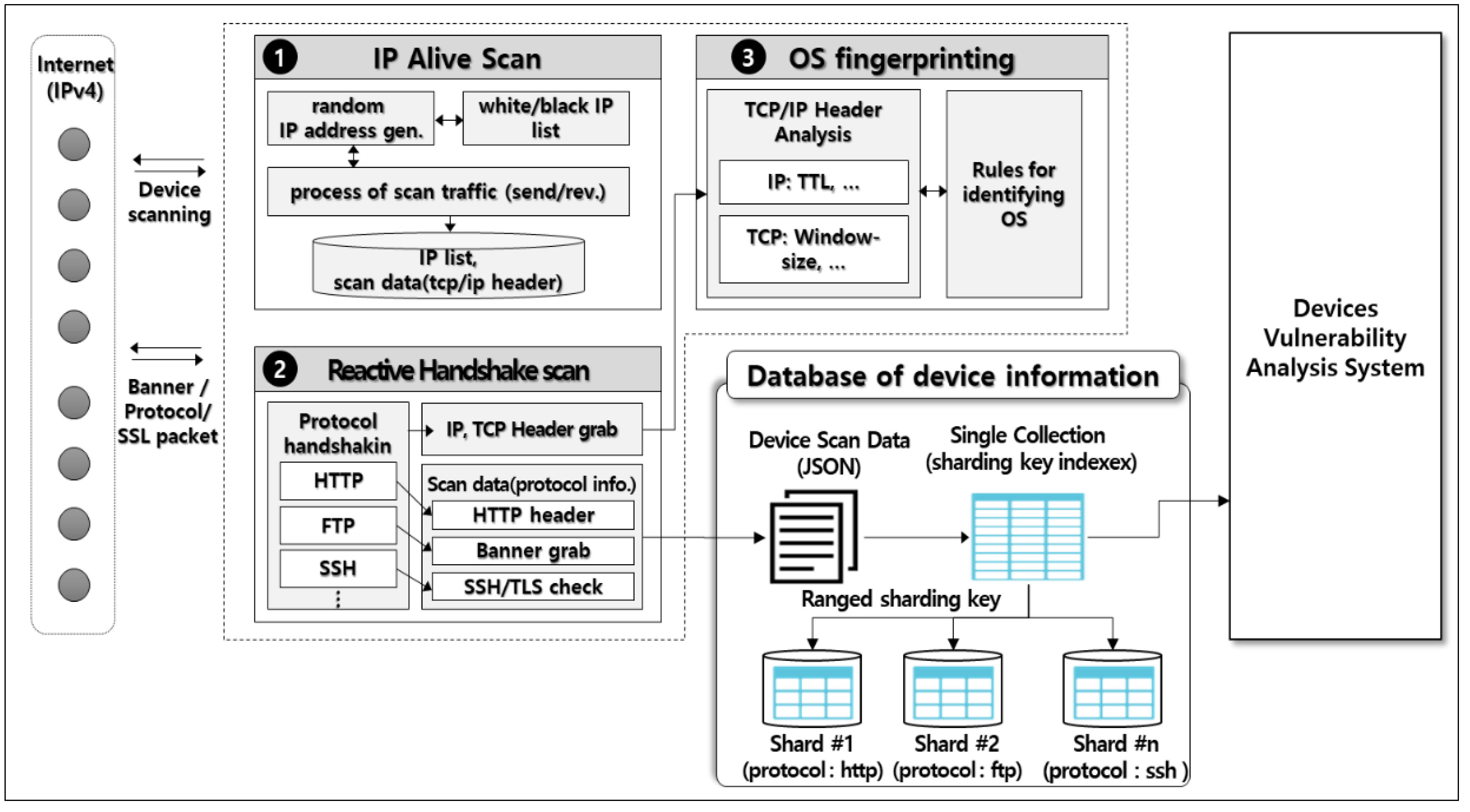
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices
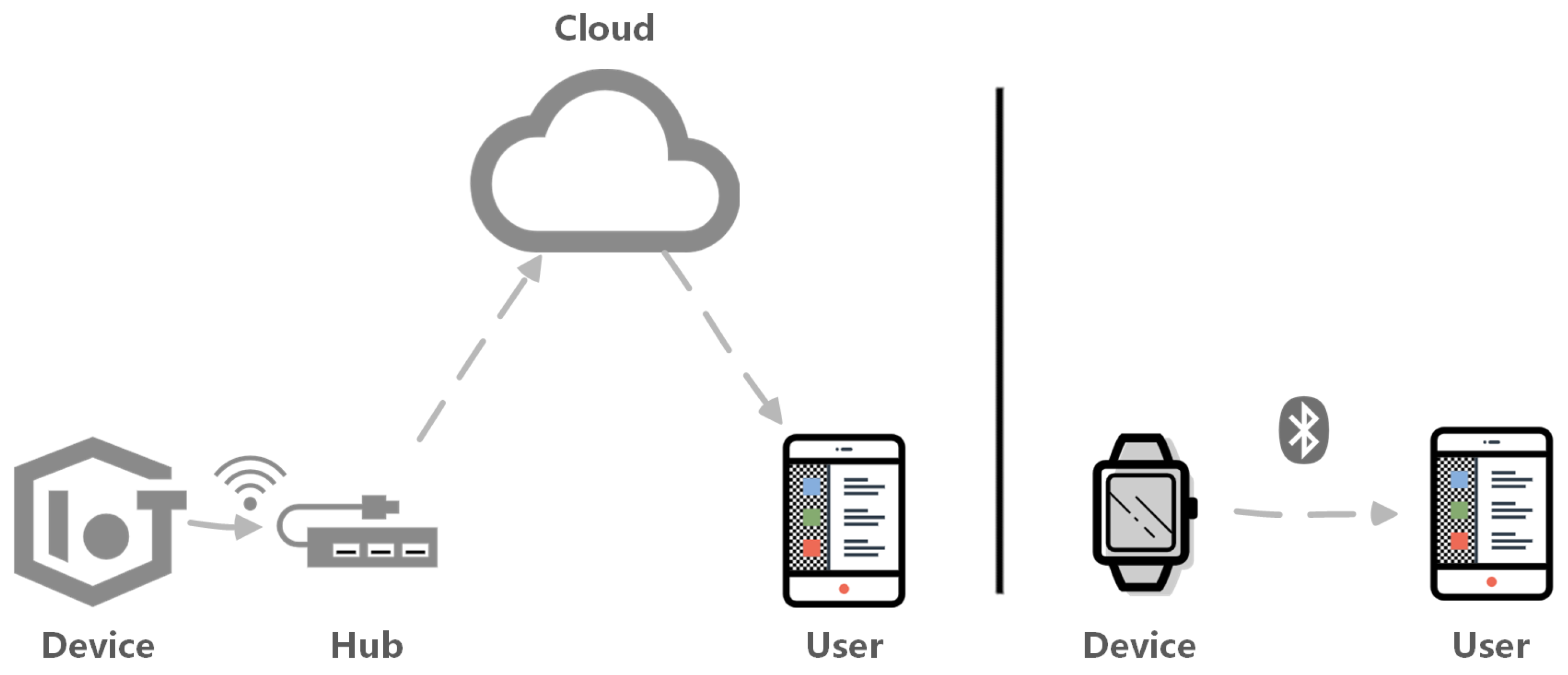
Future Internet | Free Full-Text | A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices
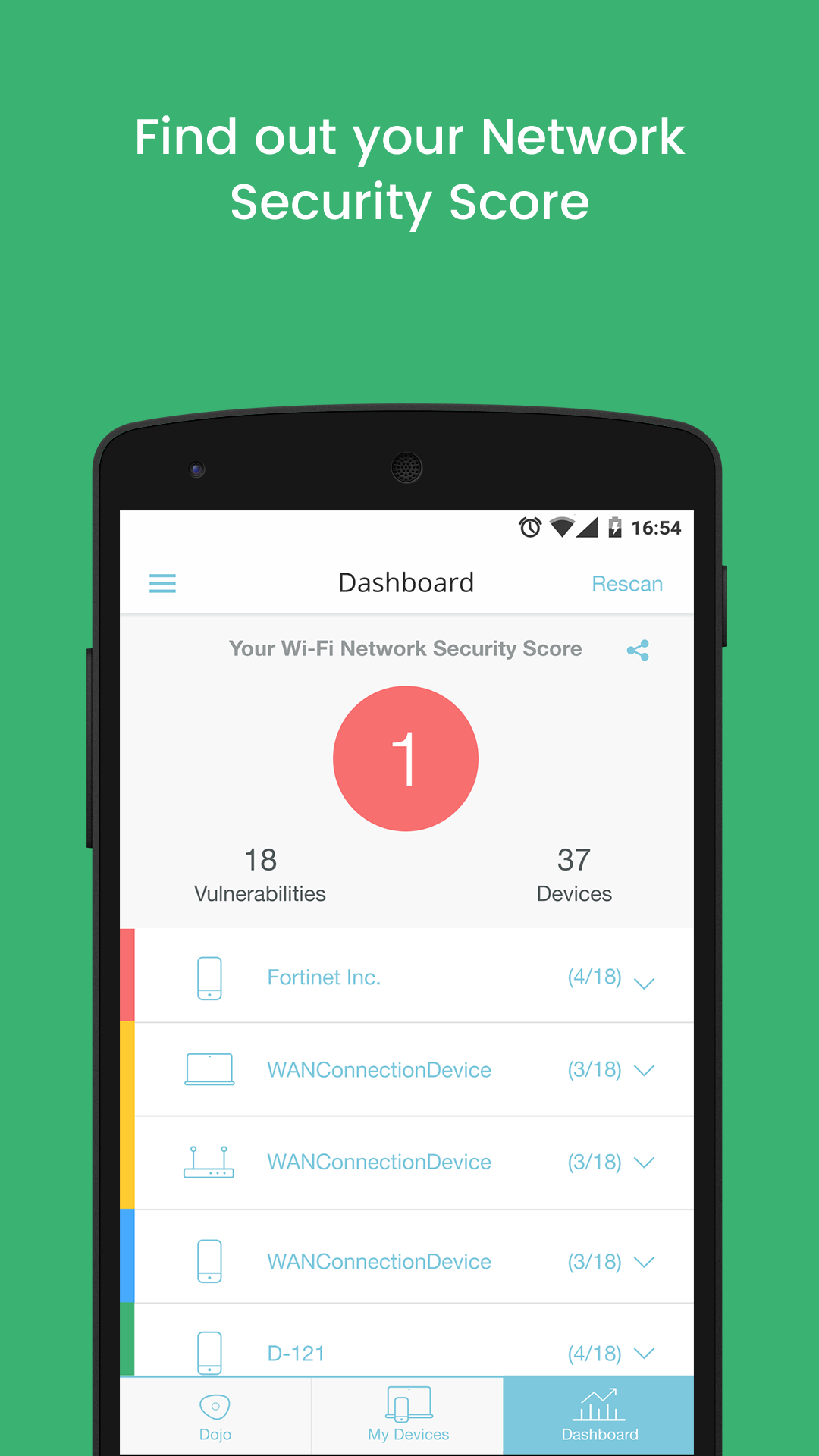
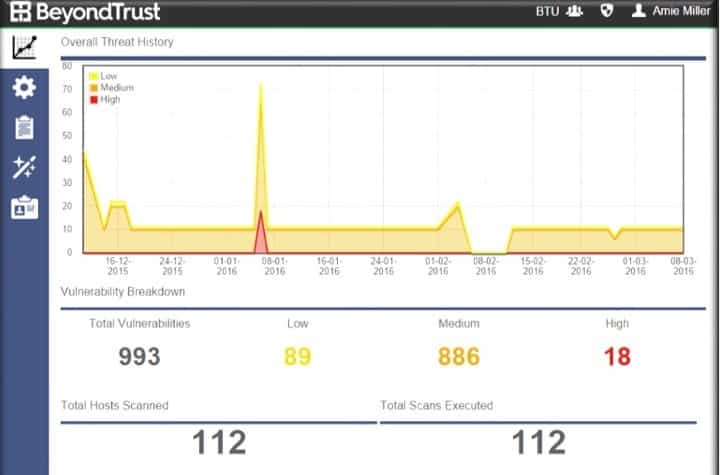
New Dojo Intelligent IoT Vulnerability Scanner App Provides Consumers With Deep Insight Into The Cybersecurity Risks In Their Smart Homes
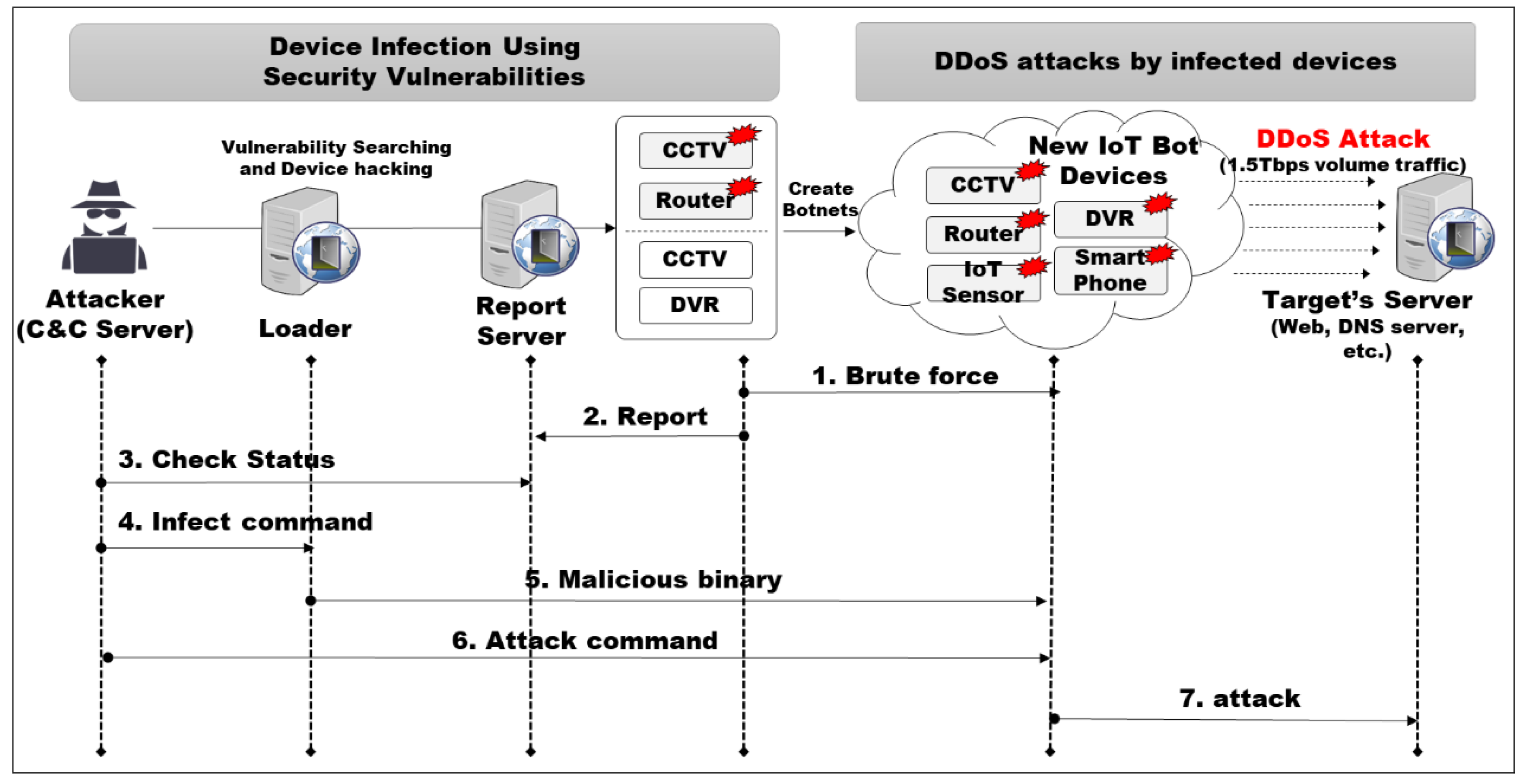
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices



![Top 5 IoT vulnerability exploits in the smart home [list] Top 5 IoT vulnerability exploits in the smart home [list]](https://www.minim.com/hubfs/iot-vulns-feature-12.jpg)