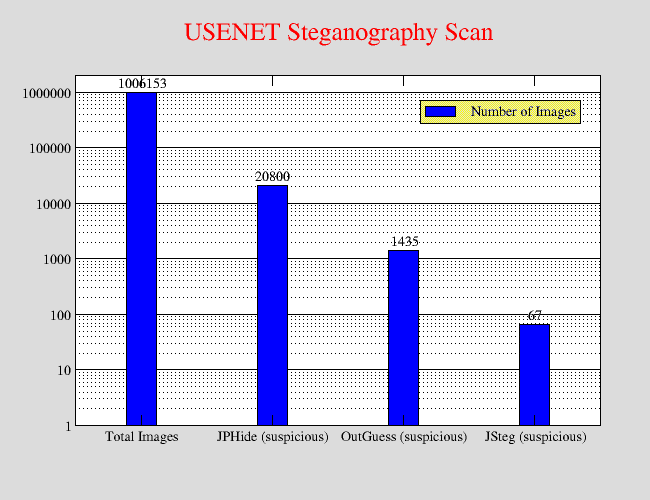
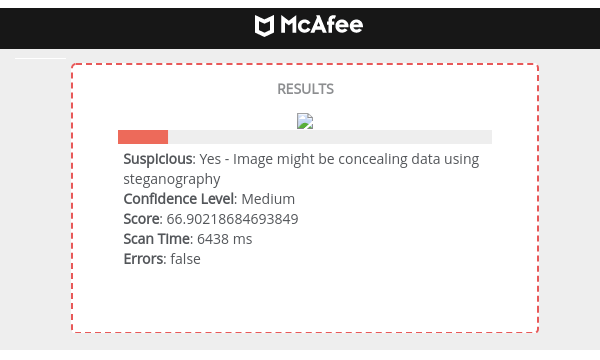
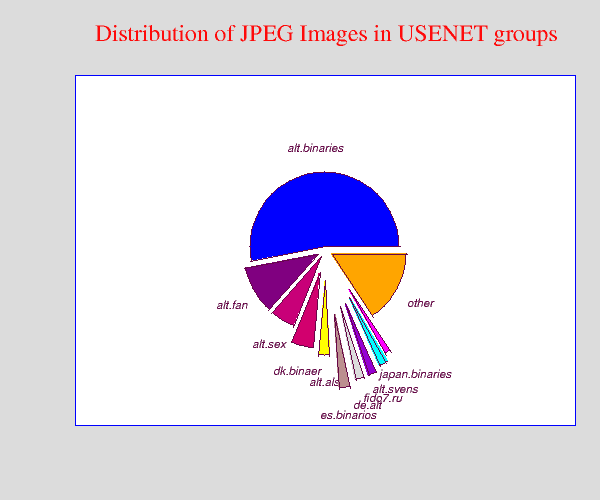
Secure Text Sharing Using Medical Image Steganography | International Journal on Recent and Innovation Trends in Computing and Communication

Sensors | Free Full-Text | A Novel Steganography-Based Pattern for Print Matter Anti-Counterfeiting by Smartphone Cameras

Architecture for medical brain image steganography using diagonal queue | Download Scientific Diagram
Proposed steganographic hiding of the crossfolded biometric image in a... | Download Scientific Diagram

SSDIS-BEM: A New Signature Steganography Document Image System based on Beta Elliptic Modeling - ScienceDirect